Cybersecurity Today: Creating Strong Passwords
Psst: CISOs and experts, this is one of our beginner-oriented articles! If you're looking for more advanced material, we recommend a dive into the...
In a world where cyber threats and data breaches are as common as a bad cold, password security is your digital medicine. Welcome to the Cybermaniacs' guide on password creation and everything you need to know about crafting unbreakable digital locks for your online kingdom.
We all know passwords are our first line of defense in this cyber battleground. From your password manager to the company's password policy to confidential information security and data to that family recipe you have under digital lock and key, strong passwords are a must. But with the increasing sophistication of hackers and their malicious tactics, it's essential to store passwords that go beyond 'password123'.
And this ain't no walk in the park! Grab your coffee, folks; it's time to boost your password game.

We're all familiar with passwords and the frustration of creating and remembering complex passwords filled with special characters and numbers. Enter passphrases, the solution to both passwords, security risks, and sanity. Passphrases are longer, memorable passwords using combinations of words or phrases, like "PurpleTiger$DancesOnMoon." They're not only easier to remember but also significantly more secure than traditional passwords. Encourage the use of passphrases to boost your defense against cyber threats.
Reusing passwords for personal accounts is a common practice, but it's also one of the riskiest, along with the ongoing problem of, let's say, "less than ideal password length". If a hacker cracks one user's password, they could potentially access passwords with the same password on multiple accounts. Emphasize the importance of using unique passwords for each account in your password guidelines, whether other accounts are personal or work-related. It may seem like a lot to remember, but that's where our next best practice comes into play.
Keeping track of numerous unique passwords for various accounts can be overwhelming. This is where password managers come to the rescue. These tools securely store your previous password and login information and automatically fill in weak passwords when needed. By advocating for the use of password managers, you simplify the authentication process and password management, making it easy to maintain a high level of security across all your accounts without the headache of memorizing a multitude of unique passwords.
Multi-Factor Authentication (MFA) is the fortress protecting your digital kingdom. It adds an extra layer of password security by requiring at least two forms of authentication before granting access to your password and user accounts. Typically, it combines two-factor authentication: something you know (your password) with something you have (like a smartphone or security token). Promote the use of MFA to provide enhanced password security, ensuring that even if your password is compromised, authentication and password information for your accounts remain well-guarded.
In the ever-evolving realm of cybersecurity, the battle isn't just about keeping hackers out; it's also about spotting them when they've managed to sneak in. Detecting intruders, especially those cunning enough to use stolen credentials, is a significant challenge for organizations.
Picture this: a cybercriminal gains access to your organization's network using stolen credentials. To most users and security systems, this doesn't set off major alarm bells. After all, the credentials are valid, so it seems like a legitimate user logging in. The intruder can gain access and then quietly navigate through the network, potentially causing significant damage before anyone even realizes they're there. This makes it exceptionally tough to spot hackers, as they move around undetected, often using compromised passwords with the same privileges as a legitimate user's unique password name.
In today's digital landscape, stolen or compromised credentials are among the most significant risks that organizations face. It's not just the loss of sensitive data that's a concern; it's the potential for severe financial and reputational damage. When an attacker gains access using legitimate credentials, they can bypass many security defenses that are designed to make login attempts and identify unusual or malicious behavior. This is why hackers frequently opt for this tactic—it's low-risk and high reward, at least from their perspective.

TTPs are the building blocks of cyberattacks. Tactics define the overarching goal of an attack, techniques detail the methods used to achieve that goal, and procedures outline the step-by-step instructions for implementing those techniques. Recognizing these TTPs is vital because it allows us to stay one step ahead of threat actors by identifying potential vulnerabilities and shoring up our defenses accordingly.
In recent years, there have been numerous high-profile cyberattacks that illustrate the effectiveness of TTP. For instance, the SolarWinds attack, where threat actors compromised software updates to infiltrate various organizations, showcased the skill and resourcefulness of hackers. Additionally, the rise of COVID-19-related scams, such as fake health organizations soliciting donations or individual users distributing malware-laden COVID-19 tracking apps, highlights the way threat actors leverage current events to exploit human emotions.
By understanding these TTPs and their importance to password policy, we can better protect ourselves from cyber threats. As we delve deeper into password policies and security, it's critical to be aware of how hackers exploit human behavior and system vulnerabilities to access sensitive information.
And... Exhale! We know that was a lot BUT password security, once relegated to simple combinations of characters, is now at the forefront of the battle against cyberattacks. It's a shifting landscape where attackers employ increasingly complex, password-sophisticated tactics.
To navigate this landscape effectively, we must grasp the significance of password security best practices. Passphrases—those longer, memorable combinations—offer a practical defense against brute force attacks. The importance of unique passwords across all accounts cannot be overstated, preventing a domino effect if one account is compromised.
Password managers provide a seamless solution for handling complex and diverse passwords, while Multi-Factor Authentication (MFA) adds a layer of security.
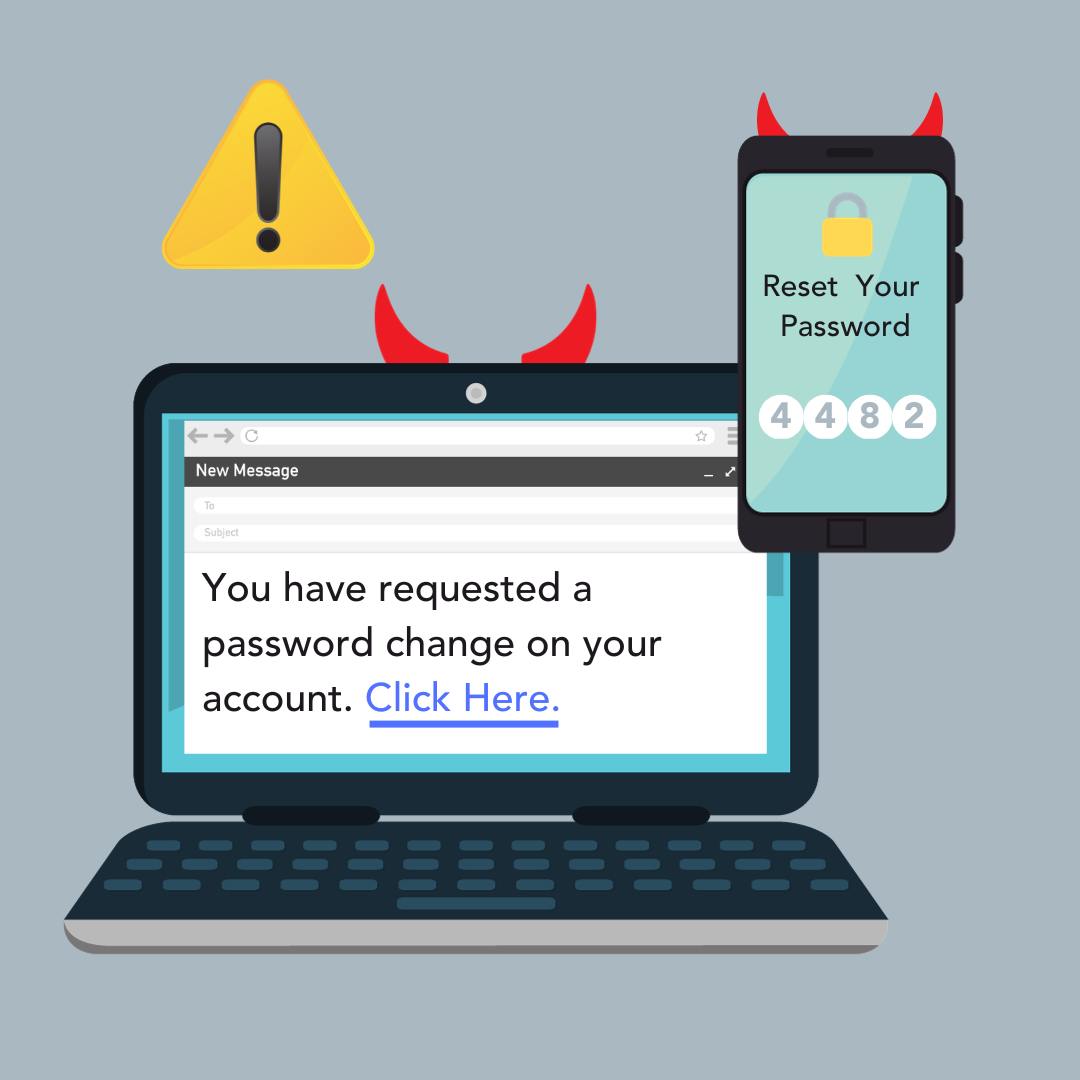
The challenges are real. Threat actors are continuously refining their tactics, and the use of phishing and social engineering techniques to force users to change passwords or to harvest valid passwords continues to grow. It's a reminder of the need for eternal vigilance, awareness, and the willingness to adapt our own security and password best practices.
By implementing these best password management practices now, we empower ourselves and our digital companions to stand strong against the evolving tide of cyber threats. With continued education, collaboration, and the integration of these password best practices back into our daily digital routines, we can collectively create a safer and more secure cyberspace. Passwords, as they stand today, are our sentinels against the dark, and it's up to us to keep them strong and resilient.

Psst: CISOs and experts, this is one of our beginner-oriented articles! If you're looking for more advanced material, we recommend a dive into the...
5 min read

In our fast-paced digital world, where passwords guard everything from your bank account to your cat’s Instagram profile, ensuring their security is...
3 min read
.png?width=1100&height=619&name=_Cyber-Saviness%20(1).png)
Here at Cybermaniacs, we believe that cybersecurity education should extend beyond the workplace to encompass the entire family. Our goal is to...
4 min read
Subscribe to our newsletters for the latest news and insights.
Stay updated with best practices to enhance your workforce.
Get the latest on strategic risk for Executives and Managers.
