The Wonderful World of Passwords
How is your Strong Password Game? In a world where cyber threats and data breaches are as common as a bad cold, password security is your digital...
Psst: CISOs and experts, this is one of our beginner-oriented articles! If you're looking for more advanced material, we recommend a dive into the blog archives!
For as long as anyone can remember, we’ve been told to have more secure passwords. Creating a strong password might seem like a tedious task that sucks up valuable time in our busy lives, but having a complex and secure password is one of the most important ways to protect yourself against potential malicious cyber activities.
Still, most users have fairly weak passwords 
Michael McIntyre: “You should probably change your password."
The 2023 Verizon Data Breach Investigations Report re-confirms the importance, as 44.7% of breaches rely on stolen user credentials, the top access method again this year, confirming a long-time trend. CISOs lament users’ poor password hygiene, yet they largely understand that only by forcing stricter requirements, do they elongate their passwords and increase their complexity.
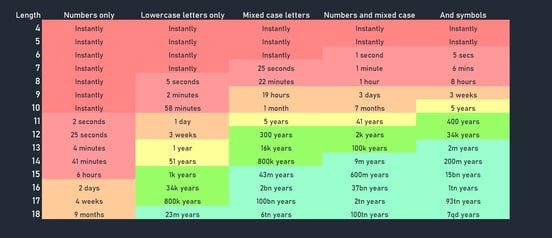
However, the frequency with which users reuse passwords (hint: Facebook and your Bank should NOT have the same password) makes those credentials a perennially interesting target for hackers. Moreover, advances in AI and machine learning enable them to expedite brute force attacks, which are made possible by users having rudimentary password constructs.
Creating a good password is hard. Remembering it is even more difficult. Having different passwords for every application and website—in a world where the average person has more than 100—is a nearly impossible task. This results in frustrating and frequent password resets. While that process is mostly secure, the help desk costs for fielding those tasks as well as the increased attack surface area created by having so many password resets mean that better solutions are required.
Here are several ways that cybersecurity leaders are trying to help the people and organizations they protect, and what individuals can do to help.
The best password is one you don’t even know! This can be accomplished in at least a couple of ways:
As with all scams, practicing proper cyber security awareness is key. Your company should ensure employees are educated on how to spot malicious activity (feel free to send this blog to your whole company). Companies can implement training and simulations or drills to get employees used to looking out for common scam techniques, prompting them to double-check whom they are dealing with and use multi-factor authentication when transferring sensitive information. Additionally, ensuring employees have strong passwords and backup authentication methods like 2FA or MFA in place will help protect against unwanted visitors trying to exploit people.
Using two or more methods (e.g. Two-Factor Authentication or 2FA) is a great way to increase security. Again, for those who may be targeted for advanced attacks, this method is still susceptible to bypass by hackers. Using a range of methods including well-crafted phishing emails, MFA is not “unhackable.”
LiStill more options exist for rethinking UserID and Password (taken together as “credential”) combinations. Startups like Nametag are looking at interesting ways to authorize users by using combinations of biometrics and trusted devices. Expect to see more new technologies arriving shortly.
Here, it is changing the mindset of users throughout the organization that will make lasting changes. The Cybermaniacs team has spent a great deal of time and creative energy to understand the psychology of the average user, and what can be done to make a lasting change in organizational culture to improve how users think about cybersecurity in every situation they face.
As with all scams, practicing proper cyber security awareness is key. Your company should ensure employees are educated on how to spot malicious activity (feel free to send this blog to your whole company). Training, simulations, and drills should get users used to looking out for the common scam techniques, prompting them to double-check whom they are dealing with and think about higher levels of security when transferring sensitive information in particular.
Knowledge is power; now you're equipped to approach your passwords better than your average bear. Whatever method or concept you employ, keep in mind that getting into users’ heads is what makes the big difference. (Call us for more on why we’re particularly good at that part!)
If you're curious about talking to someone about cybersecurity training that works: We can help.

How is your Strong Password Game? In a world where cyber threats and data breaches are as common as a bad cold, password security is your digital...
5 min read

In our fast-paced digital world, where passwords guard everything from your bank account to your cat’s Instagram profile, ensuring their security is...
3 min read
.png?width=1100&height=619&name=_Cyber-Saviness%20(1).png)
Here at Cybermaniacs, we believe that cybersecurity education should extend beyond the workplace to encompass the entire family. Our goal is to...
4 min read
Subscribe to our newsletters for the latest news and insights.
Stay updated with best practices to enhance your workforce.
Get the latest on strategic risk for Executives and Managers.
