Insider Threats and Risks: Staying Aware, Internally
Cybersecurity has become more difficult than ever in today's dynamic workplace, which is characterized by the quick adoption of remote work, cloud...
![]() Team CM
Mar 14, 2024 11:45:32 AM
Team CM
Mar 14, 2024 11:45:32 AM

In the evolving landscape of cybersecurity, the recent apprehension of a former Google engineer for illicitly sharing AI technology secrets underscores a pervasive threat: the malicious insider. This incident not only highlights the fragility of trust within organizations but also serves as a stark reminder of the critical role cyberculture plays in safeguarding intellectual property. As businesses grapple with the complexities of human risk management, this revelation prompts a deeper exploration into the strategies that foster a robust cybersecurity awareness, emphasizing the need for a proactive and inclusive approach to mitigating insider threats.
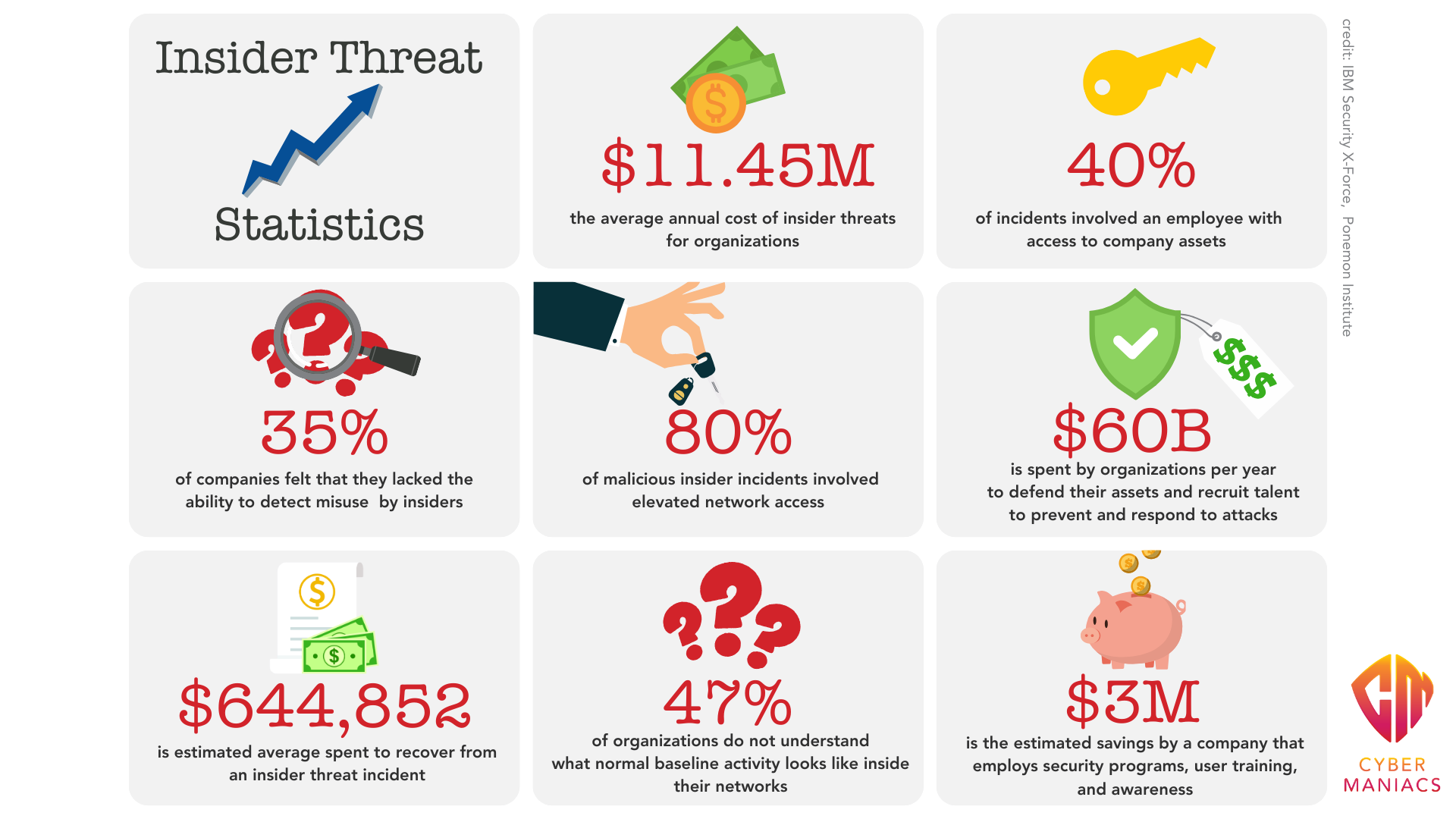
While the case of the Google Engineer is the most high-profile one, there cases of insider threats at Tesla and General Electric in the past few years illustrate the omnipresent danger of malicious insiders across various industries. Tesla’s ordeal with a former employee altering its source code and leaking proprietary data, alongside General Electric’s battle against economic espionage involving turbine technology, starkly reveals the extensive business risks tied to intellectual property theft. These incidents underscore the necessity for companies, especially those rich in IP, to adopt comprehensive cybersecurity awareness training and human risk management practices, thereby mitigating the potential for such detrimental breaches.
While cybersecurity awareness training is a critical step toward safeguarding intellectual property, it alone is insufficient in the absence of a supportive and inclusive cyberculture. Traditional compliance-based once-a-year training programs and punitive phishing simulations, fail to fully address the nuanced human behaviors that contribute to insider threats. A mere focus on compliance measures overlooks the importance of understanding and mitigating human risk. To truly protect against malicious insiders, organizations must go beyond conventional training, fostering an environment where employees are not just informed but also genuinely engaged and invested in the collective security posture.
To construct a culture of security, actionable steps, and targeted questions are essential. Here's a detailed guide:
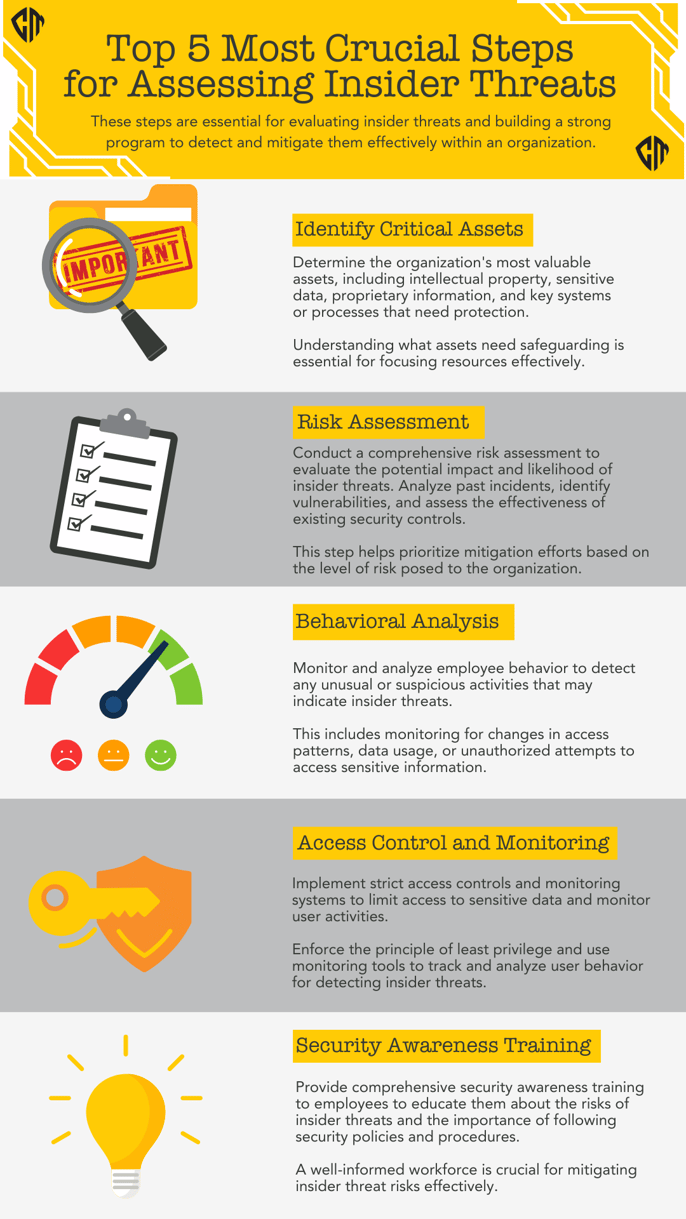
By addressing these areas with thoughtful questions and concrete steps, organizations can enhance their cybersecurity posture from the inside out, creating a more secure and resilient environment against insider threats.
Empowering Employees: Overcoming Psychological Barriers
Understanding the cyberpsychology of an organization involves recognizing the underlying behaviors, attitudes, and emotions that influence cybersecurity practices. Initially, assess the overall awareness and attitude towards cybersecurity across the organization. This assessment can reveal areas where friction, challenges, or resistance may arise, such as reluctance to adopt new security measures, skepticism towards the effectiveness of training, or discomfort in reporting suspicious activities.
To address these challenges:
By focusing on the human factors that influence cybersecurity, organizations can cultivate a culture that supports vigilant, cyber-safe behaviors.
In navigating the complex landscape of insider threats, it's clear that fostering a robust cyberculture built on trust, openness, and mutual respect is paramount. Organizations must look beyond traditional security measures to understand the intricate web of human risk management. By engaging in comprehensive culture audits, fostering environments that encourage speaking up without fear, and tailoring cybersecurity practices to address psychological barriers, companies can create a resilient defense against both external and internal threats. Let's commit to a future where cybersecurity is not just about technology but about cultivating a culture that champions security as a shared responsibility.

Cybersecurity has become more difficult than ever in today's dynamic workplace, which is characterized by the quick adoption of remote work, cloud...
6 min read

Intro: The New Insider Risk Isn’t Coming—It’s Already Here
4 min read

Understanding the Human Factor in Cybersecurity In today’s digital landscape, cybercriminals exploit not only technological weaknesses but also the...
4 min read
Subscribe to our newsletters for the latest news and insights.
Stay updated with best practices to enhance your workforce.
Get the latest on strategic risk for Executives and Managers.