Cyber Security Awareness Month: Why It Matters and How You Can Participate
Cybersecurity Awareness Month—love it or hate it, there's no denying it's like the Marmite of corporate initiatives. Every October, organizations...
Cybersecurity has become more difficult than ever in today's dynamic workplace, which is characterized by the quick adoption of remote work, cloud computing, and digital interconnectedness. While organizations navigate this landscape of rapid technological evolution, there's an often underestimated, yet highly consequential, aspect of security: insider threats.
Let's explore the realm of malicious insider threat risks and the vital role they play in a Chief Information Security Officer's (CISO) proactive stance. We'll explore the various types of insider threats, the goals that motivate these threats, and provide valuable insights into how users can safeguard their organizations from such clandestine dangers. It's time to shed light on the invisible peril within and fortify your cybersecurity fortress against internal, unseen foes.

In the cybersecurity realm, an insider is not an outsider in disguise but rather someone inherently part of the organization, holding a trusted position. It's a term used to describe employees, contractors, partners, or anyone with access to the company's systems and data. With their privileged data access and knowledge, insiders are granted the keys to the kingdom, and that's where the risk lies.
Now, what makes insider risk a fascinating yet challenging concept is that these individuals can pose a security threat, whether current or former, and they can do so either intentionally or inadvertently. It's not just the rogue employees with malicious intent, although they certainly fall into this category. Some well-meaning employees can, unintentionally, become the weak link in the security chain, often called "unintentional insiders."
You might have heard both terms—insider risk and insider threat—used interchangeably, but there's a subtle difference. Insider risk is a broader concept that encompasses the potential dangers posed by insiders, intentional or not. In contrast, an insider threat specifically relates to malicious activities carried out by insiders, often driven by personal or financial gain or vendettas.
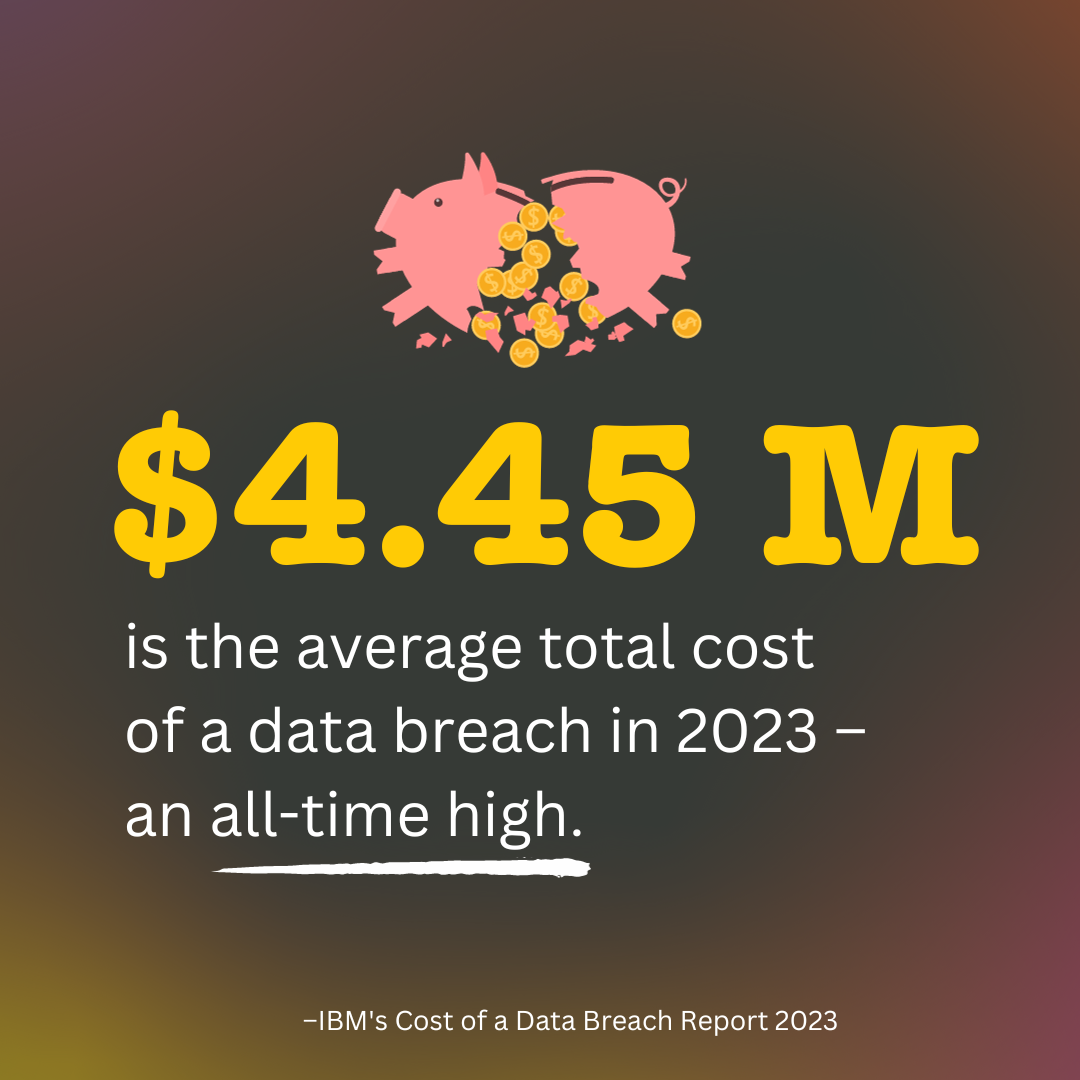
Now, let's take a quick peek at some eye-opening data breach statistics that highlight the significance of understanding insider threats. According to a recent report, about 57% of organizations faced an insider attack in the last 12 months, and a whopping 70% of organizations feel vulnerable to insider threats. This underscores the pressing need for organizations to not only secure their perimeter but also stop insider threats in their interior.
These individuals don't intend to harm the organization, but their negligence or lack of cybersecurity awareness puts the company at risk. For example, a well-meaning employee might fall for a phishing email, unknowingly giving cybercriminals remote access to sensitive customer data.
Surprisingly, it's astonishing to note that around 80% of reported insider threats fall into the category of unintentional threats because of carelessness. These incidents are often the result of employees failing to follow security protocols, whether by accident or due to a lack of awareness.
These insiders have harmful intentions to disrupt business operations, which could be driven by a desire for personal gain, revenge, or a mix of motives. Their actions can range from stealing intellectual property or other sensitive data to sabotaging the organization's operations.
These malicious insiders contribute to approximately 14% of insider threats. While this percentage of malicious insider threat indicators might seem lower, it's the one that tends to generate more severe damage and financial losses for organizations.
Sometimes, insiders become unwitting pawns in cyberattacks. Their accounts or devices get compromised, and cybercriminals exploit these security weaknesses. The insiders themselves might not harbor malicious intent but fall prey to sophisticated cybercriminal tactics.
A significant percentage of insider threats, about 37%, involve compromised insiders. These individuals become victims of cyberattacks, which can include phishing or malware, leading to subsequent breaches.
Insider and malicious insider threats can encompass a wide array of activities, each carrying its own set of risks and repercussions. Here, we'll examine some key insider and malicious threat activities that can impact organizations:
Insider threats involving sabotage typically entail deliberate actions by individuals aimed at disrupting an organization's operations. This could include tampering with critical systems, deleting important data, or compromising network integrity. The goal of insider attacks is to create chaos and inflict damage, often as an act of revenge or to further a personal agenda.
Insider fraud or insider threat detection involves deceptive activities undertaken by insiders to gain financial or personal benefits. This financial fraud could involve embezzlement, expense account manipulation, or falsifying documents. Research indicates that insider fraud is one of the most common insider threat activities, costing organizations substantial financial losses.
This activity focuses on the misappropriation of an organization's intellectual property, including patents, trade secrets, or proprietary software. Insiders involved in IP or data theft often have intentions to capitalize on or share the stolen IP. A report by Carnegie Mellon University's Software Engineering Institute found that IP theft accounts for a significant portion of insider threats.
Insider espionage involves individuals within an organization covertly collecting and disseminating sensitive information to external parties. These actors might have affiliations with competitors, nation-states, or other malicious entities. This activity poses significant national security and economic risks.
One common aspect of insider threats is the presence of compromised users. These individuals may not initially have malicious intent but are manipulated or coerced into participating in activities harmful to their organizations.
Insider threats might stem from external cyberattacks. For example, cybercriminals might compromise an employee's device and use it to then gain access to unauthorized access to an organization's network, effectively turning the employee into a compromised user.
In some cases of data corruption, malicious external entities recruit insiders by coercing, bribing, or blackmailing them into participating in illicit activities. These compromised insiders often fear the consequences of non-cooperation.
Insider threats are a shared responsibility, involving both organizations and their employees. Users need to be informed and proactive in mitigating the risks associated with insider threats. Here are some practical tips for end users to detect insider threats first:
Avoid sharing sensitive information online or discussing confidential matters on social media or public platforms. The less personal information you expose, the less attractive a target you become.
If you encounter any unusual or potentially harmful activities within your organization, report them to your security or IT team promptly. Early reporting can aid in preventing or reducing the harm that potential insider threats may cause.
Familiarize yourself with your organization's cybersecurity policies and guidelines. Know what constitutes acceptable user behavior, and what doesn't. When in doubt, seek clarification on security procedures from your IT department or security personnel.
Be cautious when receiving unsolicited emails, especially those requesting sensitive information or actions that seem out of the ordinary. Cybercriminals often use phishing techniques to trick employees into revealing sensitive data or installing malicious software.
Ensure that your devices, including laptops and smartphones, are protected with strong, unique passwords. Implement multi-factor authentication (MFA) wherever possible. Regularly update and patch your software to guard against security vulnerabilities.
In today's digital landscape, the concept of insider threats demands our attention and vigilance. By understanding the various types of insider and external threats, their activities, and their sources, organizations and employees can work together to minimize risks. Organizations must implement robust security measures and training programs to detect and prevent insider threats. Employees, in turn, should stay informed, report suspicious activities, and follow security best practices. In this shared endeavor, we can create a more secure environment where the risk of insider threats is significantly reduced.
The ever-evolving world of cybersecurity requires continuous adaptation and learning. By staying informed and working collectively, we can minimize the risks posed by insider threats, thus safeguarding our organization's critical assets and data in the digital age.


Cybersecurity Awareness Month—love it or hate it, there's no denying it's like the Marmite of corporate initiatives. Every October, organizations...
6 min read

In a world increasingly defined by digital interactions, the unveiling of the US Cybersecurity and Infrastructure Security Agency's (CISA)...
5 min read
.png?width=1100&height=619&name=The%20Current%20Landscape%20of%20Cyber%20Risk%20Management%20(1).png)
In the quickly evolving world of cyber risk management, many organizations find themselves tethered to outdated methods. Often constrained by budget...
5 min read
Subscribe to our newsletters for the latest news and insights.
Stay updated with best practices to enhance your workforce.
Get the latest on strategic risk for Executives and Managers.
